Hey {{first_name|Jedi}} welcome to the 90th edition of the Identity Jedi Newsletter. Just ten away from 100! Wow, it’s been a helluva ride. Ok this week, we are diving into the world of Customer Identity and Access Management, Decentralized Identity, and a little privacy. A lot to tackle in this edition so I’m expanding the Good Reads section to give you some extra reading material.
GOAL TO 1k!
Current Count: {{active_subscriber_count}}
Net New Subs Since Last Edition: 0 🫤
Ok, so in our first week of the Goal to 1K Campaign..we tied…lol. ( As of this writing). When you read this, the numbers might differ, as the widget above shows current active subscribers at the time it renders. And there are a couple of new subscribers pending their activation. But we can DO THIS! And I’ve enrolled some partners to help. I’ll be updating the Referral swag with some special items from some of our vendor friends. I’ll also be restocking the current swag so that some shipments will be coming your way. I’ll make an announcement of the swag details as we finalize which vendors are taking part. If you are a vendor and have some swag you’d like to offer, let’s talk!
Ok, LET’S GET TO THE GOOD STUFF!
This week's edition

CIAM..the next frontier?
Pop Quiz: What area of IAM can you legitimately say makes an organization more money?
Answer: CIAM
But it’s not talked about much it seems. And it’s probably because it’s kind of a weird space. No real direct buyer( It can be marketing, devOps, IT, and rarely security). It crosses the realm between user experience, development, and security.
But I’m going to give you a controversial reason why I don’t think we talk about it as much.
You ready?
We just don’t care.
GASP!!
We are completely desensitized to the aspects of protecting customer data. How many data breach notifications did you get this year? Another free six months of Credit Protection, yaaay!

Gif by SWR3 on Giphy
But we should care, and we should care A LOT. Because looking at the horizon and there’s a storm brewing.
Multiple regulations for customer (more on this a bit latter), increased number of AI based attacks, huge amounts of personal data already in the wild. Like that drink your best friend made in college that one time, these things don’t mix well.
Most companies DON’T have a CIAM strategy, and even fewer have it as apart of their overall security strategy.

The future MUST be decentralized
We live in a time where customer identity is more valuable than gold, yet the way we manage it is stuck in the past. Centralized identity models are out of date. They’re prone to breaches, they hoard data like it’s the 1990s, and they don’t give users control over their own information. We need a change, and that change is decentralized identity. It’s time to give people the keys to their data and let them decide when and how it’s shared.
Let me break this down: Instead of companies holding onto your data like a prize they won in a raffle, decentralized identity flips the script. It gives you control. You hold your own identity data—like your name, age, or any other attribute—and you decide when to share it. Need to prove you’re 21 to buy a drink? Cool, you can do that without also handing over your address, phone number, and middle school report card.
That’s where just-in-time attributes come into play. This is a game-changer. Imagine only sharing the exact bit of info that’s needed in the moment—nothing more, nothing less. It’s the digital equivalent of walking into a club, flashing your ID for age verification, and then walking out with your privacy intact. This dynamic access model ensures your personal data doesn’t end up everywhere, reducing the risks tied to breaches and over-sharing.
Real-World Decentralized Identity in Action
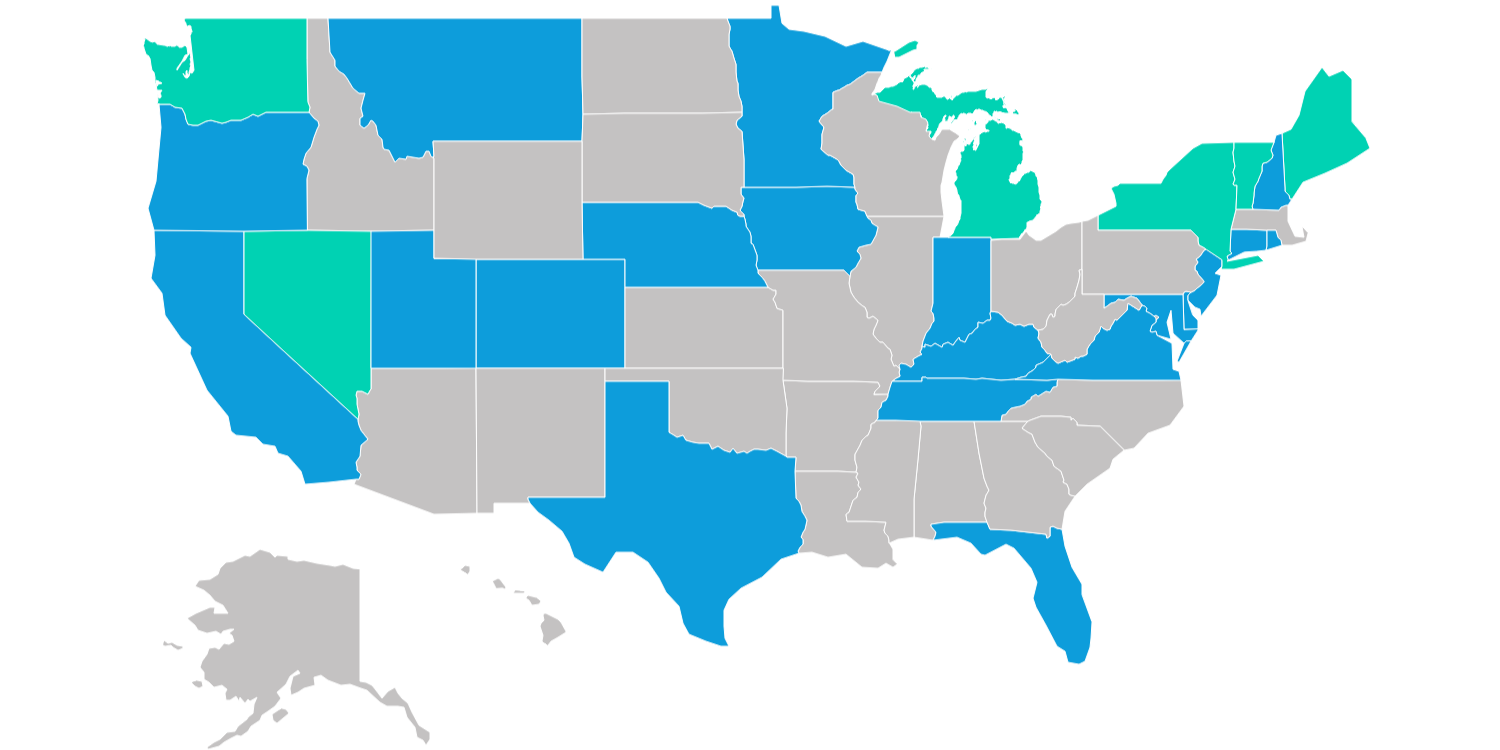
Now, this isn’t just some futuristic pipe dream—it’s happening now. States like Georgia and Colorado are already rolling out mobile driver’s licenses (mDLs). What’s cool about this tech is that it allows you to verify your identity or your age with just the information needed for that specific interaction. You’re not handing over the entire life story, just the one line they need.
For example, imagine buying a bottle of wine at the store. Instead of passing your driver’s license to the cashier and letting them see your birth date, height, and eye color, you just flash the mDL, and it confirms you’re over 21. Done. Your identity is verified, and your private info stays private.
This is already creating a blueprint for how we can expand decentralized identity beyond government-issued IDs and into areas like healthcare, finance, and retail. Think about it: if more industries adopted this approach, data breaches would become way less damaging because only the necessary data is shared—and only for the time it’s needed.
The Technical Hurdles We Still Have to Jump
Now, before we all start popping the champagne, we’ve got a few hurdles to clear. Decentralized identity sounds great, but there are still some technical challenges we need to face.
First up: interoperability. It’s a big word with an even bigger problem. If decentralized identity is going to work, it has to be seamless across multiple platforms, services, and organizations. You can’t have a system where your decentralized credentials work with your healthcare provider but not with your bank. We need these systems to talk to each other and play nice.
Then there’s security. Yes, decentralized identity is more secure than its centralized counterpart, but it doesn’t mean we’re out of the woods. If people are managing their own data, what happens if they lose their device? Or worse, what if they fall victim to a social engineering attack? We need bulletproof backup plans and safeguards that protect users from themselves (because let’s face it, people forget passwords, lose phones, and click on the wrong links).
And let’s talk scalability. Decentralized identity systems need to handle millions of transactions—every day, across all sorts of industries. It’s not easy to pull off. We’re talking about building infrastructure that’s secure, fast, and able to keep up with the demands of today’s users.
Finally, there’s adoption. Changing the way we think about identity is no small task. Most people are used to the old model. Organizations, too. There’s a certain level of comfort in having control over customer data, and giving that up is a tough sell. But here’s the thing: the shift is inevitable, and the benefits outweigh the discomfort.
Why This Future is Non-Negotiable
The future of customer identity is decentralized because it has to be. We’ve seen what happens when organizations have too much control over personal data—it gets stolen, misused, or left exposed. By giving people control over their data and only sharing what’s needed, we reduce the attack surface, enhance privacy, and, frankly, make the world a little bit safer.
Look, the technical challenges are real, and they aren’t small. But they’re not impossible to overcome. States like Georgia and Colorado are leading the way, showing us that this isn’t a dream—it’s happening. And with the right innovation, decentralized identity will become the standard.
The future is already knocking. Let’s make sure we answer.


Identity Jedi Show Podcast
The Last Word
Privacy
That’s it. That’s the last word.
Kidding.
But seriously, in the US privacy has become a mess. 20 different states have privacy laws, so good luck if you do buisness in multiple states, and I don’t see that changing. A federal standard seems to be a long way off.
Yikes.
Quick shoutout to Dan Moore and his CIAM Weekly newsletter. Some good info for tracking more trends within CIAM.
That’s a wrap for this week folks. I know Navigate was last week, don’t worry I’ll be deep diving on the announcements soon, till then.
Be Good to each other, Be Kind to each other, Love each other
-Identity Jedi